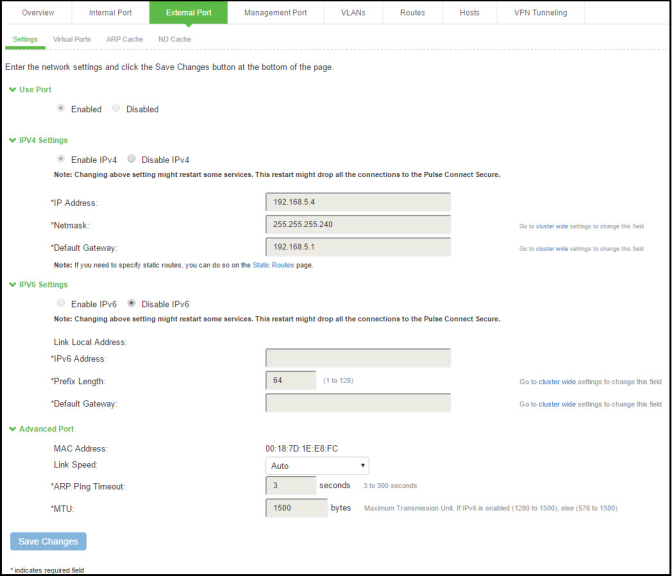
NSA Releases Future Quantum-Resistant (QR) Algorithm Requirements for National Security Systems > National Security Agency/Central Security Service > Article
Encryption Based On Nsa Suite B Cryptography Standards - No One Cares Logo - Free Transparent PNG Clipart Images Download
More than just cryptography: The performance advantages of Suite B compliance - Military Embedded Systems